Use Case

Prerequisite
1. Weblogic
Server where Web Service is running
2. Web service is target system and it requires 2 way ssl
3. We have webservice connector
4. OIM
instance
Provision Account to User
Login
to OIM instance
Click
on Users à
Search à DENNIS
Click
on Submit
Account
should be provisioned
WSDL
url on Weblogic server should be accessible
This
is target WSDL url
We are using webservice
connector
Creating Custom Certificates for weblogic server
Create
folder ServerCerts
Run
setDomainEnv.cmd from D:\Jdeveloper\user_projects\domains\Domain\bin
Run command to generate certificate
java utils.CertGen
-certfile ServerCert -keyfile ServerKey -keyfilepass keypass
copy the CertGenCA.der file from
%BEA_HOME%/wlserver_103/server/lib
directory to your newly created ServerCert dir
Run
command java utils.der2pem CertGenCA.der
Run
cmd : type serverCert.pem
CertGenCA.pem >> myCert.pem
Run
cmd : java utils.ImportPrivateKey -keystore
SeverIdentity.jks –storepass Welcome1 storepass -storetype JKS –keypass
Welcome1 -alias mykey –certfile myCert.pem
-keyfile ServerKey.pem –keyfilepass Welcome1
Copy
DemoTrust.jks into ServerCerts
copy D:\Jdeveloper\wlserver_10.3\server\lib\DemoTrust.jks
Contents
of ServerCerts
Now
start Weblogic Server and login to Admin Console
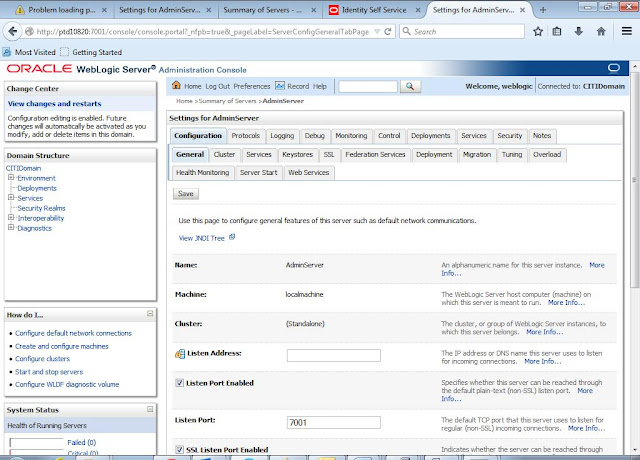
Two Way SSL Configuration for Weblogic Server
Login
to weblogic Server
Click
on Servers
Select
Check box SSL Listen Port Enabled
Click on Save
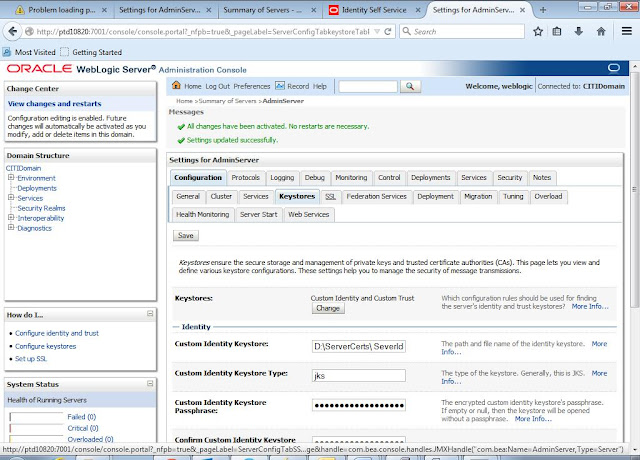
Click on Keystore tab
Configuration for Custom Keystore
Click on change
Select
Custom Identity and Custom Trust
Click
on Save
Now fill details of custom
certificates and keystore
Custom Identity Keystore : D:\ServerCerts\
SeverIdentity.jks
Custom Identity Keystore Type: jks
Custom Identity Keystore Passphrase: Welcome1
Custom
Trust Keystore: D:\ServerCerts\DemoTrust.jks
Custom Trust Keystore Passphrase:
Click on Save
Click on SSL tab
Click on Change
Select
Keystore and click on Save
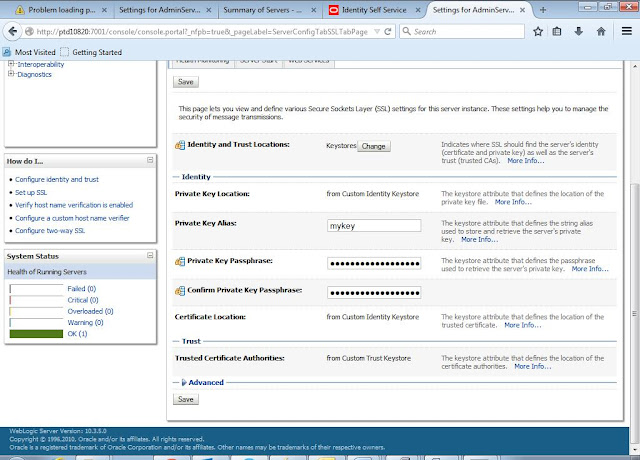
Private
Key Alias: mykey
Private Key Passphrase: Welcome1
Click on Save
 Click
on Advance
Select
hostname verification : NONE
Two
Way Client Cert Behavior: Client Certs requested
and Enforced
Click
on Advance
Select
hostname verification : NONE
Two
Way Client Cert Behavior: Client Certs requested
and Enforced
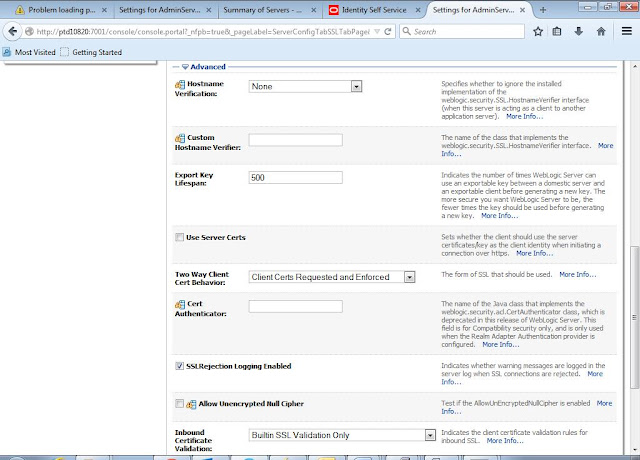
Click on Save
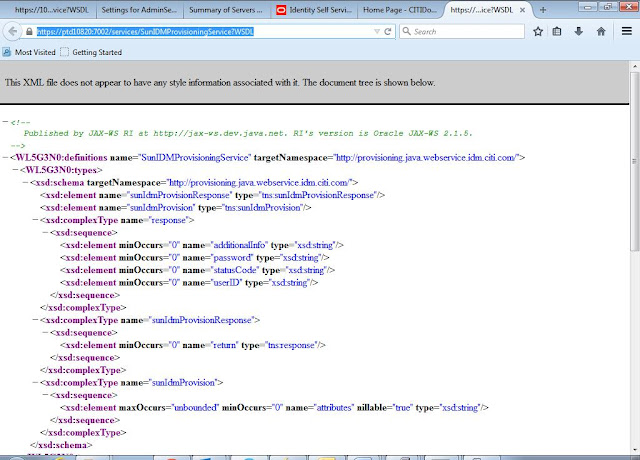
Open Firefox
This is target wsdl url
Enter WSDL url of your Web Service
https://<HOST>:<PORT>/services/SunIDMProvisioningService?WSDL
Soa Sca Deployment for SSL WSDL
1]
After enabling two way ssl for weblogic server
We
have to modify soa composite so that it points to https://<HOST>:<PORT>/services/SunIDMProvisioningService?WSDL
2]
Deploy soa composite on OIM instance
3]
Modify IT resource so that it points to new soa composite
After
step 2] deployment of SOA composite
Login to SOA server
Click
on your soa composite
Copy
URL
Login
as sysadmin
Click
on IT resource
Edit
IT resource related to AppInstace
Paste
SOA composite URL for soaServiceWSDL
Creating Certificate for SOA (Client)
Create
Directory ClientSOACerts
Run Command
java utils.CertGen
-certfile ClientCert -keyfile ClientKey -keyfilepass Welcome1
Run Command :
type
ClientCert.pem ..\CertGenCA.pem >> SoaCert.pem
Run Command :
java utils.ImportPrivateKey
-keystore ClientIdentity.jks -storepass Welcome1 -storetype JKS -keypass
Welcome1 -alias mykey –certfile SoaCert.pem -keyfile ClientKey.pem -keyfilepass
Welcome1
Contents
of directory
Configuration For SOA Server
Login to SOA serverGo
to directory
cd /home/oracle/Oracle/Middleware/user_projects/domains/base_domain
Create
Directory SSL_ptd10820
mkdir SSL_ptd10820
Copy
file D:\ServerCerts\ClientSOACerts\ClientIdentity.jks into /home/oracle/Oracle/Middleware/user_projects/domains/base_domain/SSL_ptd10820
Configure path of keystore
for SOA server
Login to EM console
of OIM Instance
User
Name : weblogic
Password : Welcome1
Select SOA -> soa-infra->SOA
Administration->Common Properties
Click “ More SOA Infra
Advances Infrastructure Configuration Properties “
Click
on KeystoreLocation
Click
on Use Multiple Line Editor
Copy
path /home/oracle/Oracle/Middleware/user_projects/domains/base_domain/SSL_ptd10820/ClientIdentity.jks
Click
on Apply
Click
on Return
Click
on Apply
Click
on Weblogic Domain which is on left pane
Right
Click on base_domain
Go
to Security -> Credential
Click
on CreateMap
Enter
Map Name SOA
Select
That MAP and click on Create Key
Fill
details as bellow
Key:
KeystorePassword
User
Name : KeystorePassword
Password:
Welcome1
Note : this is password
of keystore ClientIdentity.jks which we configured
Click
on OK
Restart SOA server
Test
1] Provision AppInstance account to User.
2] Provision Operation should be
successful.